File Database DetailsFile Database User File ReviewsWhen looking for information related to any file from our PC system, we check many sources - presently there are many web pages with information somehow related to the file names, file locations, products etc. Each user of the System Explorer application knows this situation - we knows more or less what application does the file belong to, but what it really does in the system, and is it safe or threat. On our global file database, the final scoring is composed on those criteria :
For every file, we try to check the files against the free web antivirus service : Virus Total or Jotty. This action unfortunately can be provided only if we have such file directly on our computer. For the System Explorer application user, the situation is easy : from the application itself send the file (e.g. from Processes screen) to the Virus Total service and the information about the VT scan result (using more that 40 antivirus engines) will be saved in their database with unique file identifier (mostly MD5 or SHA hash) for public use. This is step ONE in the file evaluation process. On the other hand, some file can be malicious to the computer (e.g. adwares or files taking too much of system resources - CPU, Memory, Internet connections etc.) - no antivirus will give such information, but the user can. So even file with zero negative validation from antiviruses can be marked as a threat by users - and they will be right. On the other hand - it happens frequently - some antiviruses can mark some file as a potential threat (if the inner file coding seems to carry the marks of antivirus behavior). But from the real user experience, the file is behaving correctly and is no harm to the user's computer - to the extent the user can judge (sometimes this is the stumbling-block - we the common users are not professionals in computer science and sometimes our judgement should not be the best one - do not worry in that case we take the users occurrence of the file into consideration). So these are the main criteria why the real user experience with the respective file is so important for us. And now how the judgement is done :
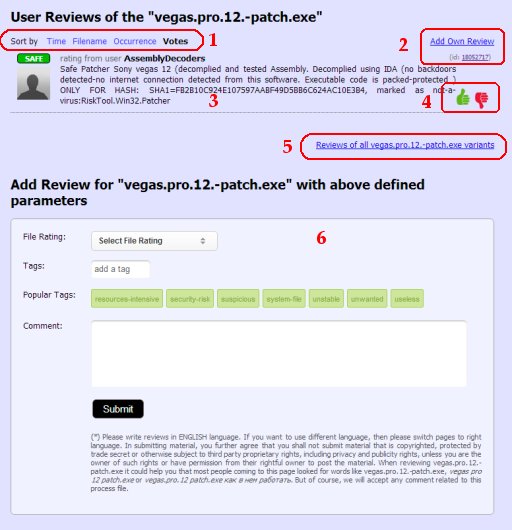
2. There are two navigation Hyperlinks :
3. File review itself. After the review is submitted by the user, it is being reviewed by our team. After the acceptance the file review is displayed among the other reviews. 4. Voting buttons : As said before, each file review can tell which experience user has with the file - by nature of such review it can be trusted or not. Any user can give + or - votes to the specific user file review and by doing so to increase or decrease the reliability of the review. The reviews with more positive votes will be preferred when displaying the list of all reviews. 5. Reviews of all variants : Accordingly to the "File ID link" when standing on page with information for just one specific file, using this hyperlink user can display the page with information for all files with this name. 6. Add file review : in this area the final decision is made by the user.
For this decision we also state that we are sure with this voting. Please bear in Your mind that it can easily end with violating the good name of the file issuing company if the voting is not fair, on the other hand the other users should be warn that e.g. some application is a fake antivirus.
Did not find answer ? Send us your question via Support Ticket.
We answer only to english, System Explorer related questions.
|