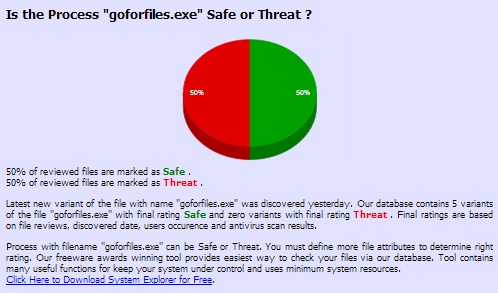
File Database DetailsFile Database Final ScoringThe final decision has come and we should judge each file if it could be a threat or safe. In many cases this is hard to say. For some files the situation is clear - if the file is a pure virus, it will be marked so and that's it. But the System Explorer database is not a pure antivirus database - we collect real user experience of working with the files. According to the user experience, some file can be marked as source-intensive (making high CPU or Memory load) - but this can be related also to other processes running in the computer, or just the power of the CPU or RAM size. Generally speaking, the real user experience is a relative and subjective scoring. To be as much honest and fair as possible and not to harm any company by just putting a "threat" evaluation for their file or application because I do not like it personally, we must gather and evaluate the inputs from as many different sources as possible and then judge the final decission based on compromise of those sources. The judgment on System Explorer side is composed of few sources :
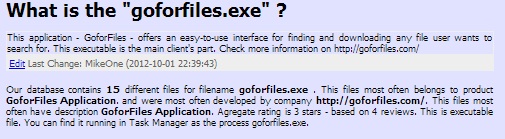
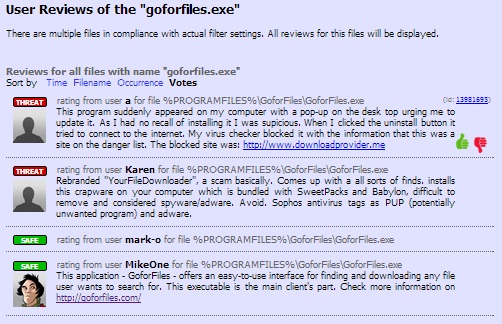
- First source, the file reviews, are taken purely from user comments for the specific file. As written above, these comments can be distorted by the user's point of view. - The discovered date is the source of reliability - newer occurrence can give most exact data. - Users occurrence means how many users detected the same file. The more users have the same file the more precise the judgment can be. - Antivirus scan results are composed against the free Virus Total service : more than 40 antivirus applications scanned the respective file and the result of it is taken into consideration. Again, the antivirus result doesn't tell You the final truth if the file is threat or safe. Another thing is that there can exist more files with the same name - and for those purposes we have two kinds of final ratings. When having just the file name selected, the final rating is related to this respective file name. When having the exact MD5/SHA variant, the rating displayed is related to this file. So for example, here is a general file selected by its name :
Did not find answer ? Send us your question via Support Ticket.
We answer only to english, System Explorer related questions.
|